Threat Risk Assessment
Our threat risk assessment encompasses a comprehensive analysis of potential risk identification and recommendations to overcome them.
Learn More
As the data privacy landscape is evolving at an unprecedented pace, we aim to maximize security of every organization. By deploying Threat Risk Assessments, Privacy Impact Assessments, Policy and Procedure Development , or Virtual CISO, we comprehend the systems, analyze their data, and implement devised solutions.
We believe digital technologies reign supreme, and our full-stack and effective cybersecurity consulting services are heavily integrated with the latest innovations to help firms build more guarded systems against cyber attacks and achieve regulatory compliance.
Contact UsOur all-inclusive compliance consultancy and due diligence approach begins with understanding organizations’ existing data privacy management systems. Our integrated team of seasoned professionals takes a holistic approach to align their practices with business goals to keep their bottom line intact. Explore our meticulously designed consulting services for regulatory compliance for HIPAA, CMMC, PCI DSS, ISO 27001, SOX, SOC Type II, GDPR and more.
Collaborate with Seasoned Consultants for Expert Guidance on HIPAA, ISO 27001, GDPR, PCI DSS, CMMC, and More
Contact Us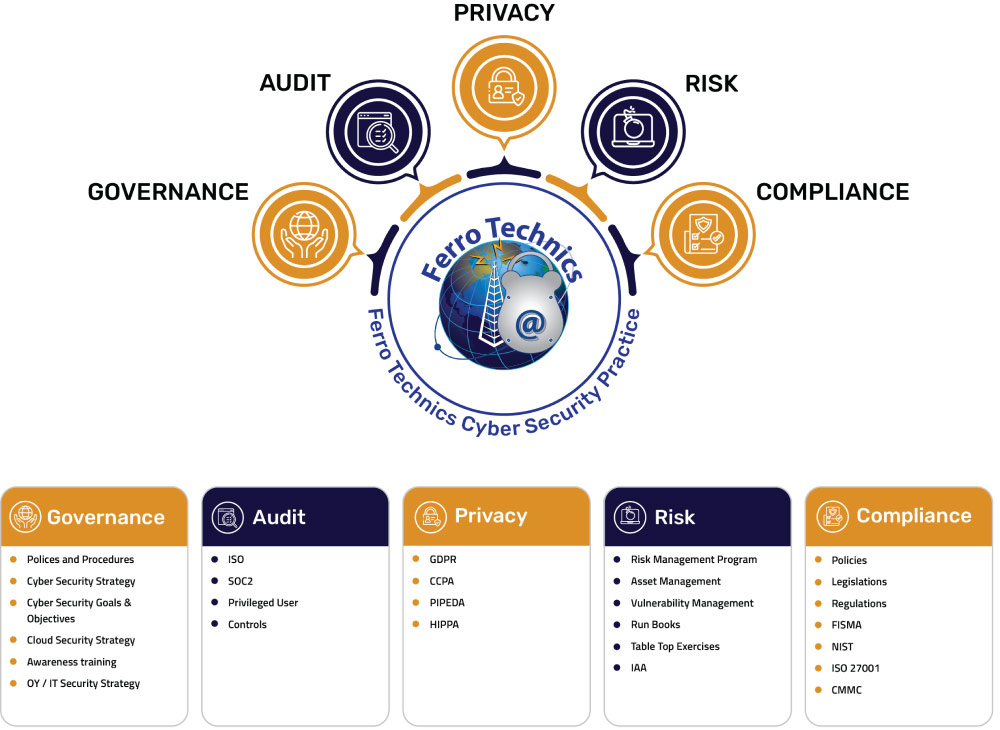
The constant risk of data exploitation and IT system vulnerability threatens organizations, increasing their need to remain in the loop for secure, protected, and integrated information systems. We discern that every firm has unique requirements, and our experienced team handles their intricacies accordingly.
Cooperating with Ferro Technics, hence, can bring enormous benefits not only for your IT infrastructures but for long-term success and regulatory compliance with HIPAA, GDPR, PCI DSS, and several other standards.
Get in Touch with Our ExpertsIn a Rapidly Technologically Transforming World, it is Uncertain What Threats Will the Next Day Bring
Book a ConsultationUnderstanding and self-evaluating weaknesses that compromise your cyber defense can be challenging, but we are here to assist. We have gathered and presented some of the most repeated queries.

IT governance encompasses a framework of procedures and strategies that aid in decision-making regarding information security systems. It further ensures that tech-related activities are in accordance with the organizations’ set goals, compliant with data privacy standards, and not prone to potential external threats.

Compliance consulting services enable organizations to adhere to industry-relevant, regional, and international security standards such as HIPAA, PCI DSS, ISO 27001, GDPR, CMMC, SOX and others. Ferro Technics compliance consulting services are aimed to analyze organizations’ privacy protocols, IT infrastructures, and overall functionality to ensure they are compliant with regulatory standards.

At Ferro Technics, we provide a suite of cybersecurity consulting services to evaluate organizations' information security systems and identify gaps attracting potential threats. These services include pen tests, vCISO, policy impact, vulnerability, security, and threat risk assessments.

At Ferro Technics, we do not compromise on our clientele and follow a holistic approach to assist them in identifying vulnerabilities by examining their existing IT infrastructures, compliance gaps, and strategic needs. Our years of expertise, end-to-end services, active communication, and customized solutions are the qualities that set our cybersecurity consulting services apart.