Guiding your Organization from Risk Assessment to Protection
In today’s interconnected world, IT assets are a valuable commodity
for every organization, and the importance of their safety from
external threats can not be overstated. Information security
programs serve as the bedrock for any firm dealing with evolving
cyber-attacks. But where to start?
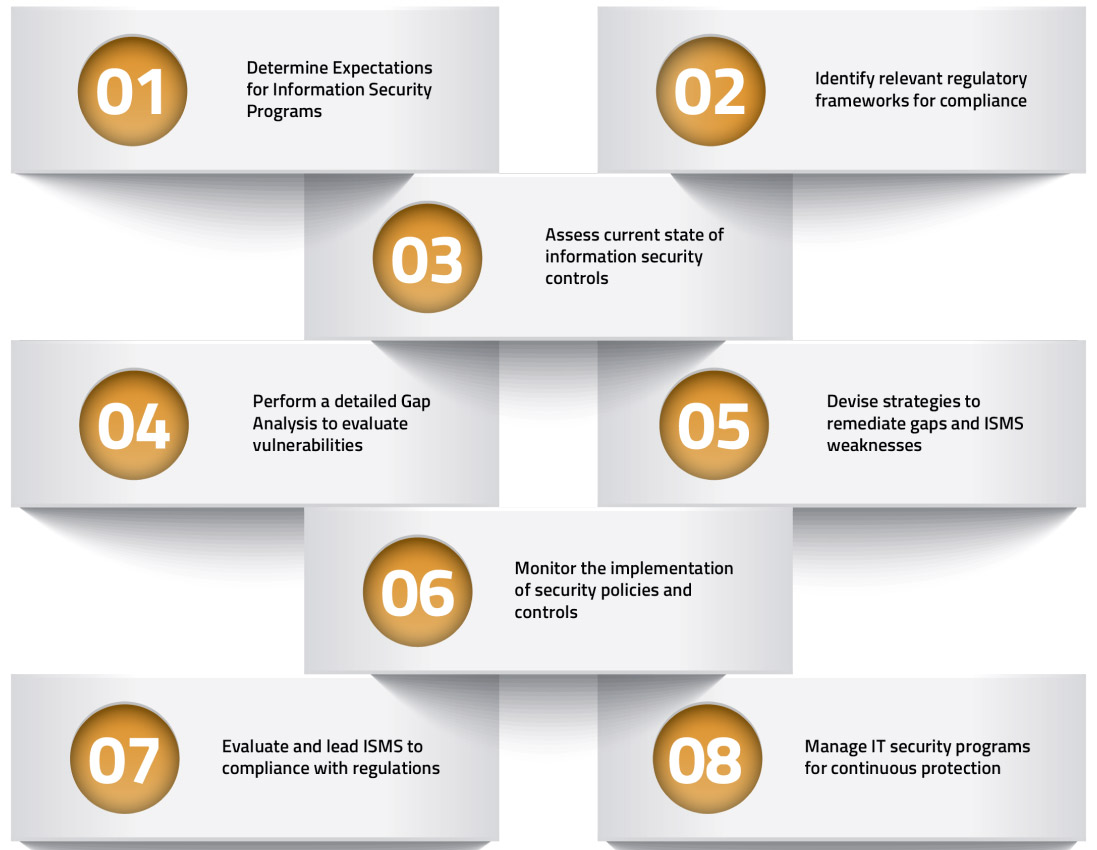
We deliver comprehensive consulting services to develop and manage
information security programs. These services include the
development of policies, procedures, processes, and initiatives
supporting the overall IT environment of your company. Our team of
cybersecurity experts will assist you in elevating your ISMS to a
level that enhances not only the safety of your confidential assets
but also supports business sustainability.
Contact Us