Phase 1: Planning
Our ethical hackers work with the organization’s in-house teams to understand the scope of pen tests, set targets, and understand goals to curate a tailored PenTest methodology.

Regardless of geographical location or industry, every business is susceptible to malicious hacking attempts. Modern-day cyber attackers wield advanced tools and techniques, making their illict efforts more sophisticated and easier for them to breach IT infrastructures.
We have been offering comprehensive penetration testing services to organizations in the Finance, Government, Education, and Healthcare sectors for almost a decade. Our ethical hacking experts simulate real-world cyberattacks to pinpoint weaknesses in businesses’ IT networks, systems, and applications. We will deploy the tech-advanced procedures while you witness your organization’s digital frontier revamping.
Contact UsAlso known as ethical hacking in the cybersecurity realm, penetration testing involves the authorized breach of IT systems. This process is conducted for organizations who seek to attain an in-depth understanding vulnerabilities their IT infrastructure possesses and weaknesses that may arise in the future. We perform penetration testing on web and mobile applications, networks, cloud, and wireless devices. The steps involve:
Crack the code of cyber resilience, unbreakable network security, and IT systems maturity with our Penetration Testing Service
Book Consultation Today!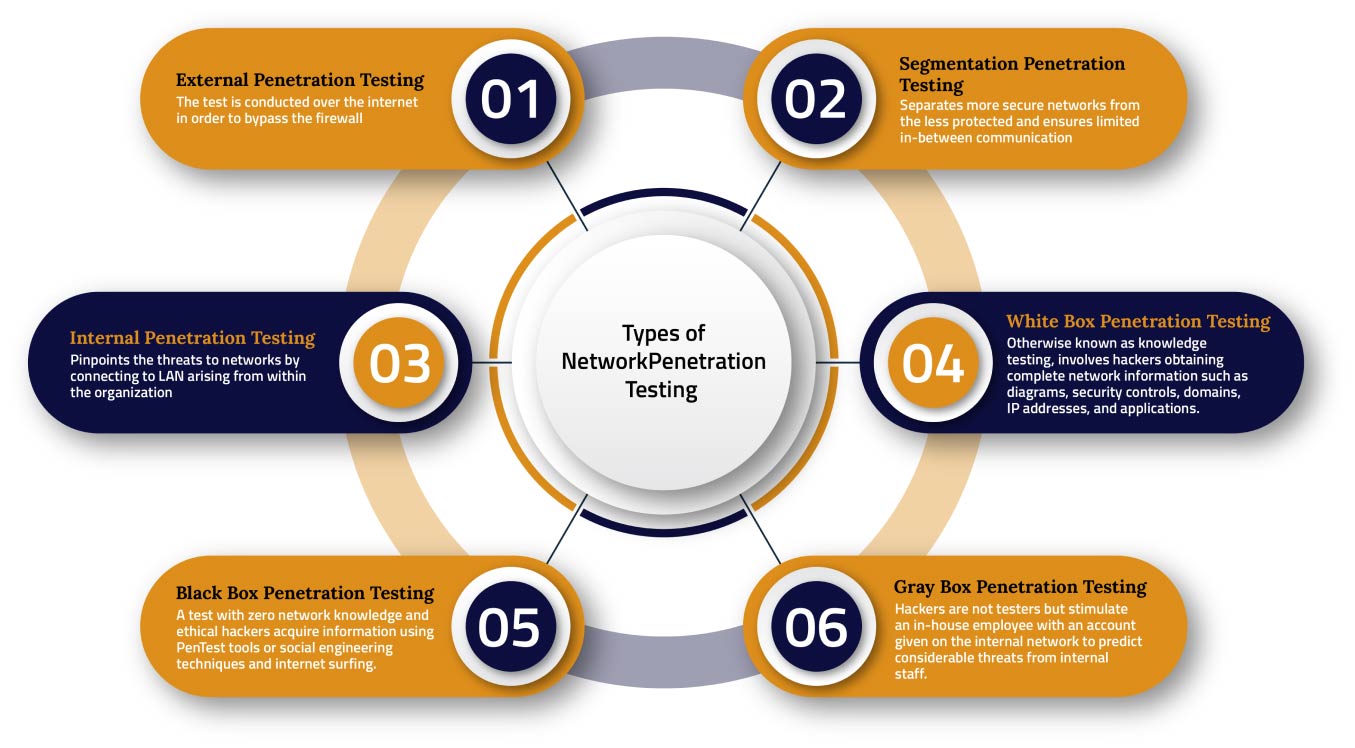
Ferro Technics is one of the leading cybersecurity auditing and consultation companies extending penetration testing services to assist your business in identifying security control resilience and IT infrastructure maturity. Using our PenTest consultation, you can reduce negative consequences such as reputation downfall, legal sanctions, monetary loss, non-compliance, severe regulatory penalties, and the list continues.
Network and IT infrastructure protection is a legal obligation put forth by PCI DSS, ISO27001, MPA, SOC2, and FedRAMP. We help your business achieve and maintain regulatory adherence.
Our expert and well-trained ethical hackers assist your company in restricting unauthorized access to assets by precisely spotting the vulnerabilities you may have overlooked.
We offer tailored, effective, and result-driven penetration testing services for your business, regardless of the company size, in the Healthcare, Finance, Government, and Education sectors.

Ferro Technics is an emerging leader in IT security, network, and infrastructure certifications. We have established a prominent presence in the cybersecurity industry due to our unwavering commitment to assisting businesses to establish and maintain robust cyber defenses, offering one of the best penetration test services in Canada.
Here is a list of most asked questions to further improve your understanding of PenTests.

Penetration testing is a proactive cybersecurity approach that simulates real-world external threats to help businesses identify vulnerabilities in their IT infrastructures. Its frequency depends on several factors, such as regulatory requirement changes, organization’s niche, and how often its system experiences technological alterations. Usually, cybersecurity experts suggest conducting penetration testing annually, especially when new upgrades, network changes, or application installations occur.

Generally, it takes a few days, but if it involves a comprehensive assessment, the tests can take up to two weeks maximum. Factors such as network size, connected devices, applications, and depth of assessment mainly influence the duration.

Automated vulnerability scanning leverages tech-advanced tools to identify known weaknesses in networks or IT systems. While it may be valuable, it often lacks comprehensive assessment delivered by PenTests. Penetration testing, on the contrary, encompasses both manual ISMS analysis and automated scanning. This allows ethical hackers to simulate real-world cyber-attacks and explore the paths that increase exploitation risks. Ultimately enabling them to curate tailored and comprehensive security posture results.

Penetration testing may have some impact on the organization’s IT infrastructures, but ethical hackers make necessary efforts to minimize disruptions. Ferro Technics team of experts works collaboratively with businesses to schedule testing at optimal times to ensure their daily operations do not experience disruption.